Table of Contents
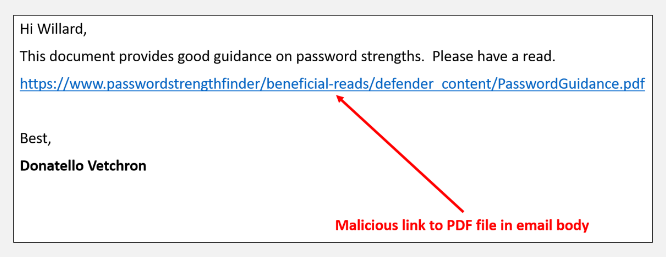
Malicious URLs are links created to promote scams or fraudulent activity. They are persuasive in nature, intending to gain sensitive and personal information. Clicking on such links can lead to a range of consequences, from having your personal data stolen to being the victim of a cyberattack.
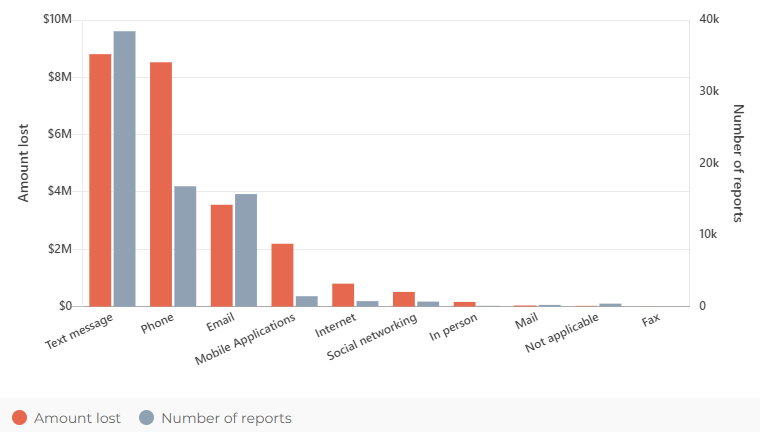
According to the Australian Competition and Consumer Commission (ACCC), there were a total of 74,567 reported phishing cases in Australia in 2022, with a total amount lost of more than $24 million.
The digital landscape has evolved since the pandemic began, and despite increased security measures, is more dangerous for users than ever. Organisations are under constant attack from well-funded professional entities that continually seek to penetrate security boundaries.
What do malicious URLs look like?
Improvements in technology and AI, paired with increased user reliance on multiple devices, have led to cyber criminals becoming more sophisticated in their approach. Harmful attacks often come in phishing emails, malware-infected web pages, or even spam messages, which cyber criminals deliver via email links, text messages, and page advertisements. These URLs most likely have embedded ‘downloadables’ including spyware, key-loggers, viruses, etc.
Malicious websites are well-recognised threats in information security, acting as an effective tool for propagating viruses, worms and other types of malicious code online.
Malicious domain owners will sometimes opt for multiple cheap domain names (such as xqerty.com), which is one method of identifying the difference between a safe and malicious URL.
Today, with hybrid and flexible work an integrated part of many workplaces, it remains a priority for security teams and cyber advocates to detect and protect against the spread of malicious links via email.
How to protect against a malicious URL in 2023?
Here are seven strategies to protect against malicious URLs:
1. View certificate details
Just because the connection is secure does not mean you know who is on the other end of that connection. Most browsers (like Edge, Chrome and Safari) allow users to view the certificate by clicking the padlock icon.
2. Use online resources to detect malicious URLs
VirusTotal is a website that analyses suspicious URLs. This site uses numerous antimalware engines and will report URLs associated with malware or other malicious activity. Also, make sure you have Safe Browsing checks turned on in your settings.
3. Check the domain
If you are eager to know who is running a website or want to check whether it is safe, you can leverage a few tools. Sites such as MX Toolbox and https://Who.is can tell you the email address registered with the website and the registration date. Sites like these can evaluate the website itself and cross-check for any red flags. Malicious domains are likely to have been registered very recently – always treat new domains with suspicion.
4. Regularly update your systems
A common tactic leveraged by cyber criminals involves scanning devices for vulnerable applications. Regularly updating your operating systems, applications and plugins will provide better protection against malware.
5. Use reliable web filters
Web filters can be used to prevent malicious URLs from entering an organisation’s network. These layers of security offer protection by blocking malicious websites and malicious downloads, as well as malicious software such as spyware, Trojans and rootkits.
6. Utilise authentication measures
Authentication measures are also important. Two-factor authentication (2FA) is an incredibly effective way to verify legitimate users. 2FA requires users to provide more than one form of identification when logging in, such as a username/password combination and an ID token or biometric scan. This helps protect the system from cyberattacks.
7. Enlighten your employees and your customers
Employees must know how cyber criminals use malicious URLs against organisations and take steps if they suspect suspicious behaviour online. There are many ways organisations can ensure staff understand these risks, including mandatory training sessions, email alerts of new threats, and regular newsletters highlighting recent scams and security concerns.
Experteq protects your team against malicious URLs
With the rise of cyberattacks and malicious code, security teams have now prioritised detecting and protecting against them. Businesses today are vulnerable to malware, ransomware and other types of cyberattacks daily. We offer cybersecurity solutions tailored to your business needs to protect your networks from these attacks.
Experteq specialise in comprehensive security and cloud solutions that protect both your business and your customers. Our team focuses on cybersecurity management, including analysts who determine the focus of a cyberattack and take steps to address those attacks.
Visit our cybersecurity page for more on how we can protect your business.

