Table of Contents
While this is not the most intuitive recommendation, research has found that when periodic password resets are enforced, passwords become less effective as users tend to pick something weak, then use it in a rotational pattern. If a user creates a strong password: long, complex and without any pragmatic words present, it should remain just as strong in 60 days as it is today. It is Microsoft’s official security position to not expire passwords periodically without a specific reason. The so-called “complex” passwords are not as secure as they seem and only adds to helpdesk costs.
Microsoft’s position for password best practices are as follow:
- Maintain an 8-character minimum length requirement (longer is not necessarily better).
- Eliminate character-composition requirements.
- Eliminate mandatory periodic password resets for user accounts.
- Ban common passwords, to keep the most vulnerable passwords out of your system.
- Educate your users not to re-use their password for non-work-related purposes.
- Enforce registration for multi-factor authentication.
- Enable risk based multi-factor authentication challenges.
Azure AD and EM+S features that can help you achieve password protection in the new “Cloud First” era.
Turn on Azure AD Password Protection and Smart Lockout
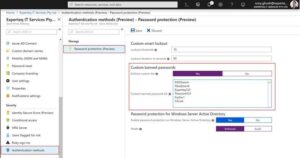
Azure AD Password Protection and Smart Lockout are now in public preview. Help your organisation to ban common passwords to keep the most vulnerable passwords out of your system (point 4 from the list above).
- Protect accounts in Azure AD and Windows Server Active Directory by preventing users from using passwords from a list of more than 500 of the most commonly used, plus over 1 million character substitution variations of those passwords.
- Customize your Azure AD smart lockout settings and specify a list of additional company specific passwords to block.
For point 6 and 7 we can use the below built in Azure AD and EM+S features
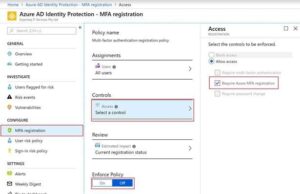
Set up Azure Identity Protection policy to force users to register for MFA
Azure AD Identity Protection MFA registration policy can be used to manage the roll-out of MFA registration for all users. Once the policy is enforced, all targeted users will be prompted to verify their details to register for MFA.
User Authentication Options
Different Authentication methods can be set up from the Azure AD Multifactor Authentication Management portal. Before enabling MFA, your organisation must determine what verification options to allow. It is important to allow more than a single verification method so that users can authenticate in different scenarios. Notifications through the Authenticator app is the recommended method which is the most secure, and also provides the best user experience.
Turn on Conditional Access baseline policy to require MFA for admins
Use Azure Active Directory Conditional Access policy to enforce Multi-Factor Authentication for privileged Azure AD accounts in the organisation. The baseline policy is in public preview, and available to be turned on by default for your tenant.
The following Azure AD roles are covered by this policy:
- Global administrator
- SharePoint administrator
- Exchange administrator
- Conditional access administrator
- Security administrator
Recommendation: Exclude at least two emergency-access administrative accounts to make sure you don’t get locked out of the tenant.
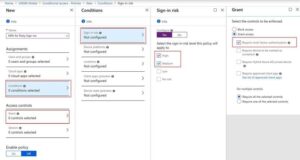
Set up Azure Identity Protection and Conditional Access for Risk Based MFA challenges
MFA is a great technology, but enforcing MFA on its own leads to an “always on” implementation, that may create MFA fatigue impacting user productivity. Azure AD Identity Protection “sign-in risk” indicates the likelihood (high, medium, or low) that a sign-in attempt was not performed by the legitimate owner of a user account. It is recommended to use the sign-in risk level, with the Conditional Access policy, to require MFA only for risky sign-ins.